I’m aware of what constitutes a decent password, but typing in 15-30 random characters each time I lock my computer screen is starting to get a bit taxing.
How secure does my user password really need to be and what are the threats to it? Does the same apply to a root-enabled user as a “regular” user when it comes to password security?
For context, my threat model doesn’t need to account for real people breaking in and accessing my computer, the damage would be very contained.
Bonus question - what are the risks of having a weak password on a root user on a spare laptop on the same network as my main device that is used exclusively for web browsing? Thanks.
This is an interesting table for password cracking based on password hash…
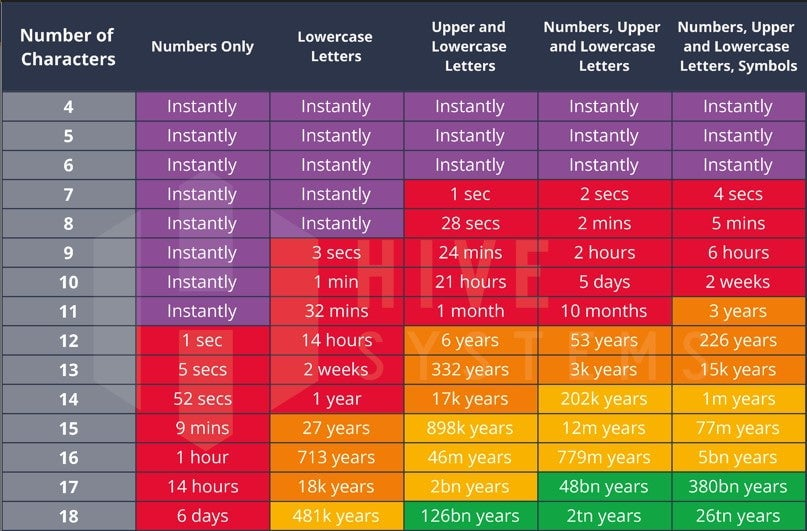
I was wondering why 1 year was in the red category, but then I realized that that time could decrease quite a bit over time with technological advances
EDIT: typo
The chart also doesn’t specify what hardware the calculation is based on. If it’s “1 year to crack for your average desktop PC”, then a server farm will do so in minutes.
This is for random characters but “interestingpassword” will get cracked by a dictionary attack almost instantly.
For context, my threat model doesn’t need to account for real people breaking in and accessing my computer, the damage would be very contained.
I mean if you don’t have open ssh ports on your computer or whatever I don’t think you need a strong password, given that you’re not concerned about physical access. I would say that at the very least have a reasonably secure root password (/user password if you’re a sudoer/anyone else who can get root permissions with your user account) because if you end up with some malware on your computer that can, say, enter passwords, you don’t want it to be ridiculously easy to bruteforce.
Great! This is the kind of answer I’ve been looking for. Thank you.
deleted by creator
No biometrics! Just wanted to clarify the only difficulties related to typing my password are its length
Physical security is more important than software security on laptops. In a public space it’s enough to have a shit password as long as there is one.
For ssh ports or remote desktop connections that don’t use pairing you definitely need a strong password. For local WIFI connections it’s not as important as your WIFI security though.
I use a pretty simple password in my PC and Laptop, since, in theory, I’m the only one with access to them (oh, and my wife, of course).
I just don’t have ssh enabled and the root passwords are ridiculously strong.



