Cyberattacks against water utilities across the country are becoming more frequent and more severe, the Environmental Protection Agency warned Monday as it issued an enforcement alert urging water systems to take immediate actions to protect the nation’s drinking water.
About 70% of utilities inspected by federal officials over the last year violated standards meant to prevent breaches or other intrusions, the agency said. Officials urged even small water systems to improve protections against hacks. Recent cyberattacks by groups affiliated with Russia and Iran have targeted smaller communities.
Some water systems are falling short in basic ways, the alert said, including failure to change default passwords or cut off system access to former employees. Because water utilities often rely on computer software to operate treatment plants and distribution systems, protecting information technology and process controls is crucial, the EPA said. Possible impacts of cyberattacks include interruptions to water treatment and storage; damage to pumps and valves; and alteration of chemical levels to hazardous amounts, the agency said.
…
McCabe named China, Russia and Iran as the countries that are “actively seeking the capability to disable U.S. critical infrastructure, including water and wastewater.”
We could do that… or we could raise rates again for the third time this month and record another year of record profits. After much consideration, we’ll do the latter, but you better be ready to bail us out if we get hacked.
Water and sewer are overwhelmingly public utilities in the US. This is more a case of small-time bureaucratic incompetence than corporate avarice – think along the lines of your grandpa writing the default Wifi password on the front of the router because he can’t remember it and doesn’t know how to change it, except Grandpa is in charge of a rural water district, and the router is the control system for the chlorine treatment.
Where water service is expensive in the US it’s usually because decades-old infrastructure built to support far-flung suburban development are starting to fall apart, and there was never a plan to pay for replacement. Some places are also being required by the EPA to separate ancient combined storm and sanitary sewers, which basically entails a complete replacement of the sewers at a cost of billions. Infrastructure is expensive to maintain, especially if you spend a few decades ignoring it first.
And when the rural communities can’t afford to do the EPA mandated updates, they sell out to a publicly traded, for profit corporation…who raises basic utility fees multiple times over the short span they’ve owned and operated the infrastructure of the rural communities.
I’m not saying you’re wrong in every instance, as what you’ve said holds true a lot of the time. Just not in this very specific, albeit anecdotal, instance.
So there is also the classic issue of underfunding of municipal services. Good luck getting qualified security people for what local government pays.
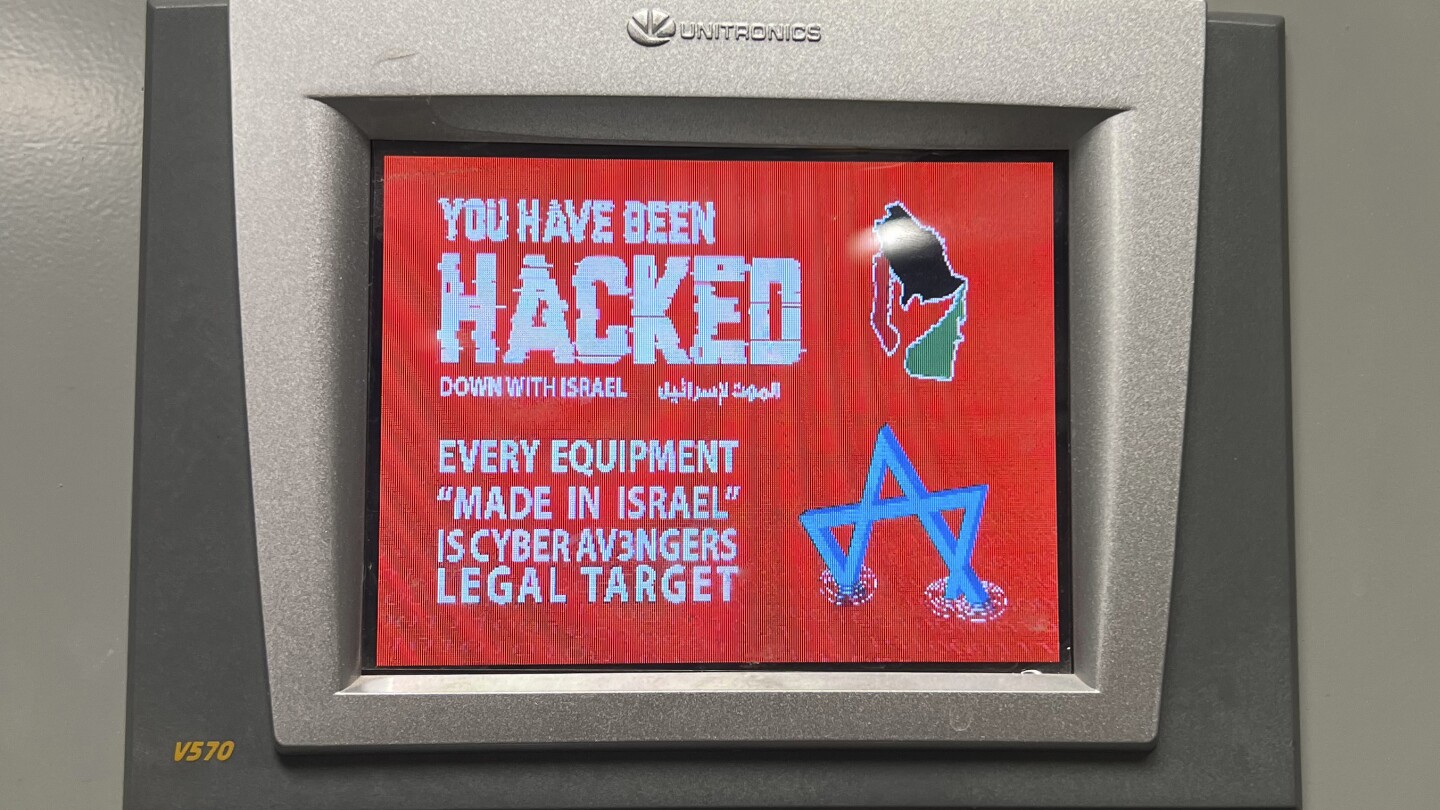
Why are any of them not air gapped?
I’ve worked on SCADA systems for water automation in a municipal water supply. The meters, valve positions, and sensors can have a tunnel back to the main office and generally aren’t accessible unless someone physically breaks into something. With a proper remote solution it’s pretty secure (as secure as anything, anyway) to access and manage things from anywhere cutting down water waste and time when problems occur.
The issue, as usual, is people. I can’t tell the story, but I can say that managers and higher ups at municipal water departments will override decisions to make things more accessible without proper protections because they refuse to understand the concept of even the most basic security. Not every water department, obviously, but I can absolutely point to several that will demand easy access with no VPN because they want to use their fucking home computer, and when you won’t provide it they’ll hire someone else who will.
I’ve worked on networks for water systems as well and you are right, the problem is people. Weak or default passwords, little to no physical security, it all comes down to the people in charge.
In this side of networking, typically accessibility is considered more important than security as they don’t want to be locked out of something in a pinch. With recent hacks, the opinion is changing, but slowly. The industrial world moves at snails pace compared to the enterprise side. They operate on a if it’s not broke don’t fix mentality.