Wow, this is a very complex exploit, involving bits of iMessage and an undocumented CPU feature that allowed the attacker to evade hardware memory protection. From what I can see, Lockdown mode would have prevented this. The attacker is ridiculously skilled regardless
Exerpts from the article missing from the bot summary:
The mass backdooring campaign, which according to Russian officials also infected the iPhones of thousands of people working inside diplomatic missions and embassies in Russia, according to Russian government officials, came to light in June. Over a span of at least four years, Kaspersky said, the infections were delivered in iMessage texts that installed malware through a complex exploit chain without requiring the receiver to take any action.
With that, the devices were infected with full-featured spyware that, among other things, transmitted microphone recordings, photos, geolocation, and other sensitive data to attacker-controlled servers. Although infections didn’t survive a reboot, the unknown attackers kept their campaign alive simply by sending devices a new malicious iMessage text shortly after devices were restarted.
The most intriguing new detail is the targeting of the […] hardware feature […]. A zero-day in the feature allowed the attackers to bypass advanced hardware-based memory protections designed to safeguard device system integrity even after an attacker gained the ability to tamper with memory of the underlying kernel.
someone was made fun of one too many times about having green bubbles in imessage
The true villain origin story
i’m a bit of a texter myself, you know…
Seems like the definition of advanced persistent threat.
It isn’t persistent over a reboot, but the tested devices received new corrupted iMessages immediately after reboot
Persistent in APT isn’t referring to the malware itself, but rather the threat actor. I meant that this seems like a textbook APT actor.
It’s important to reboot your devices frequently
Can’t wait to listen to the Darknet Diaries interview about this in a few years.
How do you find those podcasts, sometimes the stories are really interesting but I think he is running thin on ideas.
not op, but I think it depends a lot on the person he’s interviewing
deleted by creator
I recently invented a “People First” Cybersecurity Vulnerability Scoring method and I called it CITE, Civilian Internet Threat Evaluation with many benefits over CVSS. In it, I prioritize “exploit chains” as the primary threat going forward. Low and behold, this new exploit, although iOS, possibly one of the most sophisticated attacks ever using one of the longest exploit chains ever! Proof positive!
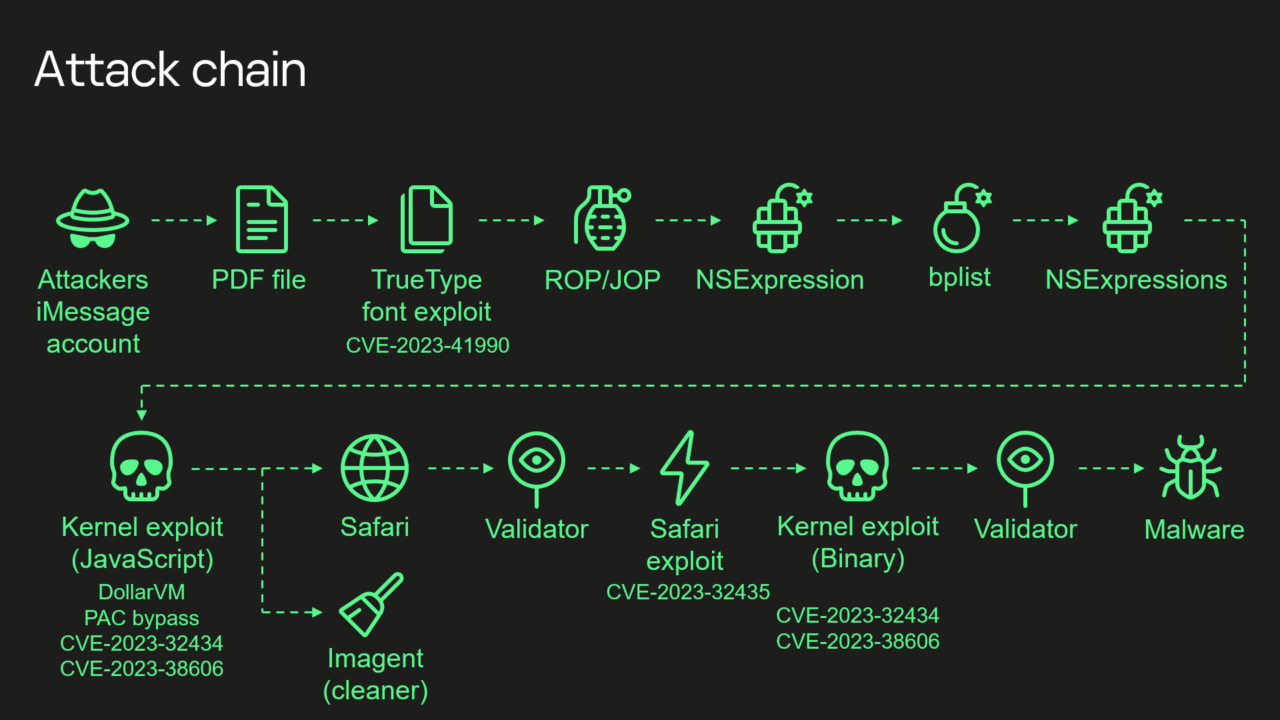
Depending on how you define it; I define the Kaspersky diagram has 8 steps. In my system, I define steps that advance the exploit discretely as stages, so I would evaluated Triangulation to be a 4 stage exploit chain. I should tally this attack to see how it scores and make a CITE-REP(ort).
You can read about it if interested. An intersting modeling problem for me was does stages always equate to complexity? Number of exploits in the chain make it easier or harder to intrusion detect given that it was designed as a chain, maybe to prevent just that? How are stages, complexity, chains and remediation evaluted inversely?
Thanks for sharing! I’m amazed at how sophisticated this was.